Themida Unpacking: One Breakpoint, Zero Execution
Themida is a well-known software protection tool designed to prevent reverse engineering and analysis. However, by leveraging a single hardware breakpoint, it is possible to unpack a Themida-protected binary without executing any of its code. This approach minimizes risk while allowing for further analysis.
Themida employs multiple layers of protection, including anti-debugging, obfuscation, and virtualized code to obscure the binary. Typically, unpacking requires execution, which can trigger unwanted behaviors
Exploit
We first disable Themida’s anti-debugging features using ScyllaHide. This tool bypasses anti-debugging checks and ensures that the debugger can attach to the process without interference.
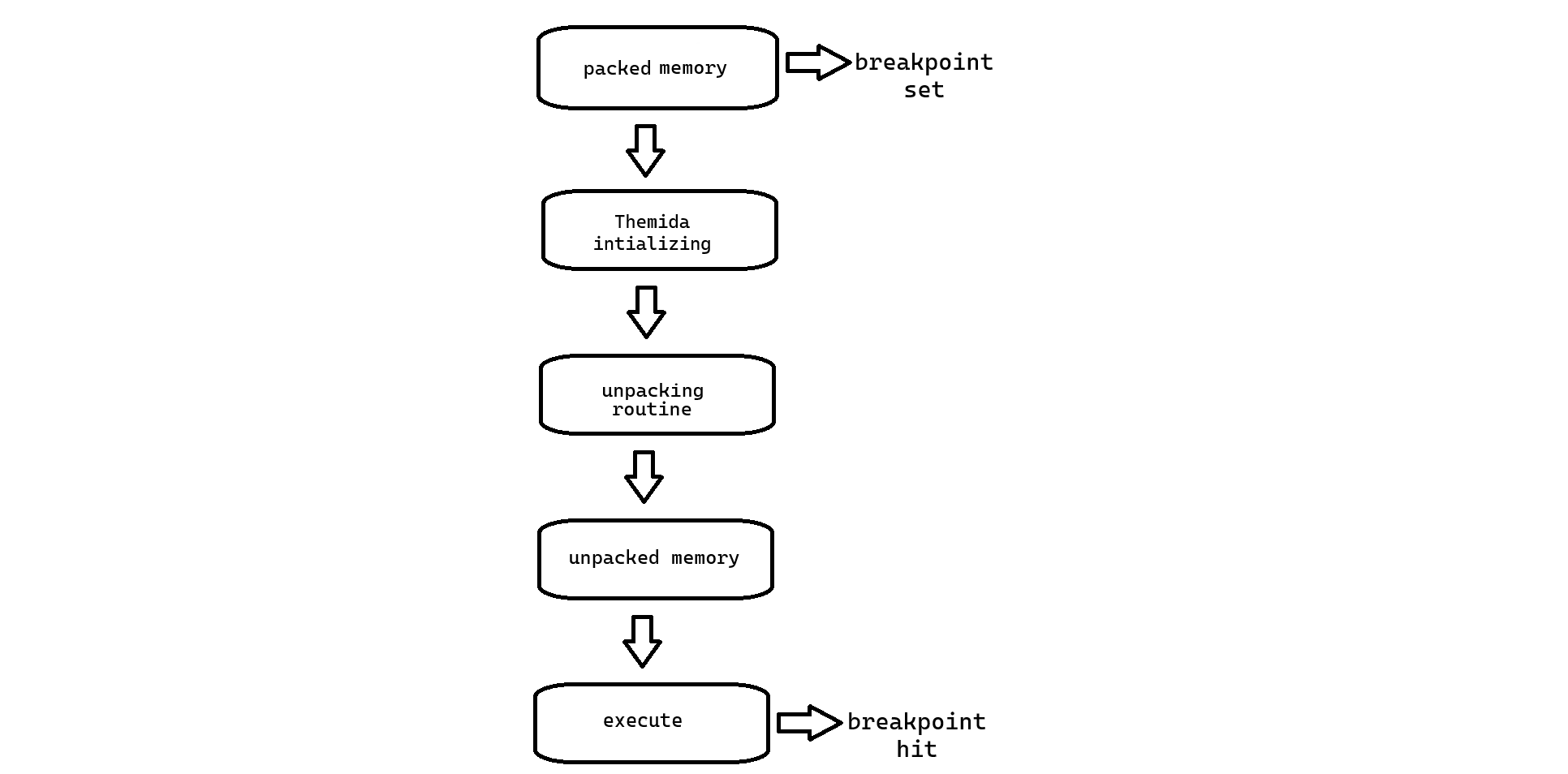
Next, a execute memory breakpoint is set on the .text section of the binary, Which is the first section header in the binary
Once the breakpoint is in place, we execute the binary. The execution stops at the breakpoint immediately. This allows us to inspect the memory, where we find that the Import Address Table (IAT) has been fully restored and the binary is in its unpacked state.
Conclusion
Using this method, the packed binary is successfully unpacked without executing any user code. This is useful for analyzing potentially malicious or unknown software while avoiding the risks associated with execution.